The Most Secure Way To Use CryptPad

Photo Dietmar Rabich Wikimedia Commons CC-BY-SA
A French translated version is also available.
You're looking for a privacy-focused collaboration tool? Well, you already found it! But what does “privacy” in this context actually mean? And how is it technically enforced? Are there any additional precautions needed for an extra-safe usage of CryptPad?
In this blog post we will answer these and other questions. We will show you in which scenarios CryptPad is secure, and give you ideas for concrete actions for using CryptPad safely. While we do as much as possible to make CryptPad secure, its security also depends on how you use it.
🧑🏫 Preliminaries
🗺 Threat model
When speaking of security or privacy, we should always define the scenario we are speaking of. This scenario is the so-called threat model which defines the adversarial capabilities. In general, we aim to think of them to be as powerful as possible. If we can defend against a strong adversary, we can also defend against a weaker one.
The first assumption about the adversarial capabilities follows directly from CryptPad's architecture. CryptPad is a web application: you visit the website of your instance (e.g., https://cryptpad.fr) and automatically download the client code that will be executed locally on your computer. If you receive bogus code from this server, you cannot establish any security, as this bogus code may, as an example, send all your documents in plaintext to the server. Hence, you must trust the server to not run any active attacks (i.e., not to run a modified CryptPad server software).
We nevertheless defend against an honest-but-curious (i.e., passive) server. The second assumption is thus that the server plays according to the rules, but could try to infer sensitive information by analyzing all the data it receives. This scenario includes the possibility that a third-party gets access to the server and can see all data and logs. CryptPad has already defended against such an adversary in the past when a third-party instance was seized by the police. We therefore consider this scenario to be highly realistic.
Lastly, we assume the attackers to have network capability. This would be the case for the system administrator managing the network in your office, your internet service provider, or secret services as well as many others. The attackers may even use active network capabilities, that is they can sniff your web traffic, and also replay, drop or modify data sent over the network.
🔑 Cryptography
One of the key features of CryptPad is end-to-end encryption. Let us give you a rough idea of what encryption and authentication are. There are three main building blocks:
- Symmetric Encryption (or secret key encryption) works similar to a box with a lock: We can put something into the box and lock the box by key (encryption). Only someone with the key can unlock the box and access the content (decryption) and modify it. Since the same key is used to lock and unlock the box, this scheme is dubbed symmetric. We can further make copies of the key and distribute it to people whom we trust, so that they can all lock and unlock the box.
- Asymmetric Encryption (or public key encryption: PKE for short) differs
from symmetric encryption in that a different key is used for encryption
(namely, the public key) and decryption (the private key).
You can imagine asymmetric encryption as the following system: you distribute
open locks (the public encryption key) to everyone and keep the (secret
decryption) key to yourself. Then, if someone wants to send you a message,
they put it in a box and close a lock on it.
Thus, only you can open it while anyone can produce a locked box for you.

- Digital Signatures are closely related to physical seals: Only the
persons in possession of the seal (which we call the signing key) can sign,
but all other people can verify the authenticity of a document using the
public verification key of the emitter.
In addition, digital signatures also guarantee that no one is able to modify
the sealed content without readers noticing it. A property that regular
seals don’t enjoy.
Note that there is a symmetric variant of this primitive called message authentication code. However, it is rarely used as an independent building block and is jointly used with symmetric encryption to achieve authenticated encryption, that further guarantees that messages are not tampered. As we exclusively use authenticated encryption in CryptPad, we usually use “symmetric encryption” instead in the explanations for simplicity, but actual guarantees are stronger.
For CryptPad, we combine all of these building blocks to achieve different goals. We will explain the usage below in the section pertaining to Documents.
🧗 The Basics
We outline some basic measurements that allow you to significantly increase the security of your CryptPad usage:
- CryptPad is open source software and as such there are various instances running it. While we host the flagship instance you might choose a different one depending on the jurisdiction for instance.
- Ensure that you are connecting to the chosen CryptPad instance over HTTPS.
- All security mechanisms are only as strong as your password is. If your password is easily guessable, attackers can get full access to all your data stored on CryptPad. We recommend you to either generate a random password using a password manager or to choose multiple words in case the password needs to be memorizable. Use this password only for CryptPad to avoid other services leaking it.
- Log out of CryptPad after each session to require the password to access your data on CryptPad. Otherwise, anybody with access to your device can also access your data on CryptPad.
- Use two-factor authentication in your account to add protection against phishing by adding a temporal factor to your login. A user guide is available in this blog.
🧑 Contacts
As we will show below, adding your peers as CryptPad contacts lets you more easily and safely share documents. You can moreover restrict access to a document to specific contacts and exchange text messages with them.
The easiest way to add someone to your contacts is to share the link to your profile over a secure communication to your peer and request to add each other as contacts.
⚠️ Note that usernames are not unique on CryptPad. Depending on context, it may be wise to verify a received contact request through another secure channel.
📄 Documents
CryptPad uses symmetric encryption with a per-document secret key to make your documents unreadable for anyone who has no access to their corresponding keys. CryptPad also allows you to differentiate between read-only and write accesses to a document. For that, anyone wanting to modify a document needs to prove that they own the private signing key linked to the document. For this, they sign their modifications and other people working on the same document can verify that the modification was indeed done by an authorized person before accepting the changes.
♻ Sharing
CryptPad keeps these technical details “under the hood” and provides a simple interface to share documents via links. Such a link essentially contains the symmetric key for encryption and decryption, for verifying signatures as well as the one for issuing signatures (in case of read/write access) in a non-revokable manner.
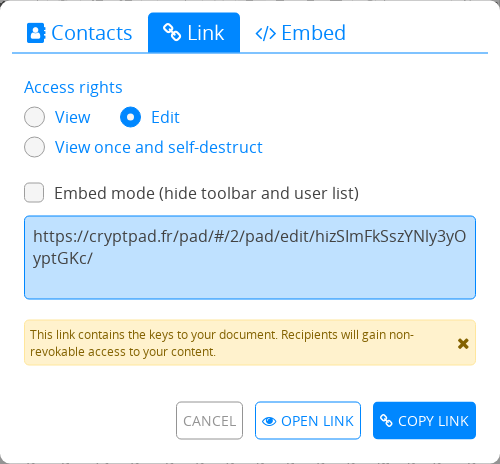
⚠️ This implies that the document is only as safe as the weakest communication channel used to send these links.
If you consider a channel to be unsafe, or if it is publicly accessible, you may want to isolate some of your documents from it. For instance, you can limit the sending of edit links to Signal chats with disappearing messages.
Another possibility to safely share the access is to send it over CryptPad to your contacts. It internally uses the “mailbox” system for internal communications, without the CryptPad server knowing better. This way, you do not have to use a secondary (potentially insecure) communication channel.
⚠️ Note that CryptPad documents contain the full edit history by design. It is easily accessible to anyone from the user interface. If you made a manipulation error, such at past some text you didn’t want to share, while producing the document before sharing it, we recommend that you copy-paste the version you want to share for collaboration in a new pad before sending it to sanitize the history (it also helps to track changes afterward).
⛔ Restricting Access
As CryptPad operates with static keys, granted shared accesses are not revokable. This means that by default anyone who was granted access will forever be able to read (and modify) a document. To prevent this, you can shut down access to a document using the Access List feature.
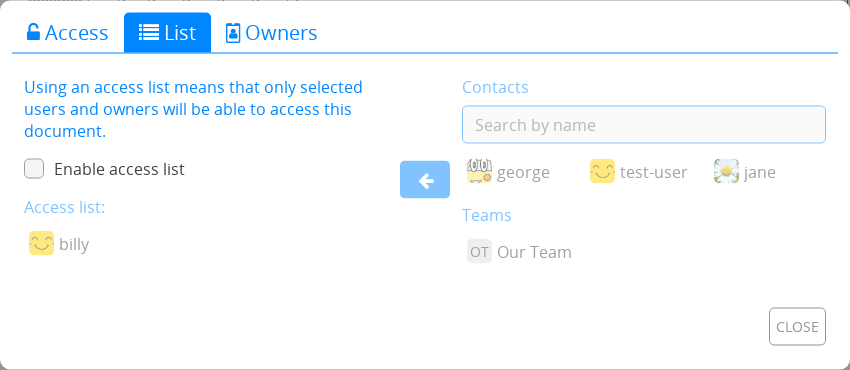
This way, only the selected persons have access to the document, independently of who has received the sharing link.
Also make sure you or your team is set as “owner” when you create documents. This will give you full control including the possibility to destroy a document if it contains sensitive information or the link escapes your control.
🔒 Per-Document Passwords
For additional safety, you can protect a document with a password. The document is then only available if you have both, the sharing link and the password. This is especially useful for the case where you do not have a secure communication channel to share the link, as you can send the link and the password over two distinct channels (e.g., text messaging and email). This way, the attacker has to monitor on both channels at the same time which makes it a lot more difficult.
When you share documents with your contacts directly on CryptPad, communications are encrypted, and we assume that you want to give them access. Therefore, the password is remembered and sent with the document when you share it. The recipient, or yourself, are not asked for it when opening the document. This implicitly assumes that the security of CryptPad drive is at least as strong as the communication channels used to share the document.
💨 Self-Destruction
CryptPad allows you to make self-destructing documents which will be destroyed either after the set expiration time or after the shared document was opened the first time.
This feature is especially useful if you have to share sensitive data that should not be accessible forever. You could use it to share a password to a peer for example.
🕵️ Anonymity
CryptPad only provides a weak form of anonymity and does not hide your IP address or your “user agent” (browser and operating system). The server can furthermore theoretically link IP addresses of people who are often collaborating on the same documents. Of course, we do not run these analytics for our flagship instance, but we want you to have to trust us as little as possible. You may want therefore use the following tools and techniques:
- The Tor browser to connect to CryptPad and hide your IP address.
- A burner account that is only used for specific high-risk actions such as working on a small set of documents or publishing sensitive information to prevent the possibility of linking IP addresses of collaborating people.
- Tails for leaving no traces on your local device.
💡 Other Tools
CryptPad is designed to be a general, easy-to-use office suite. As such it may not always fit your specific needs. We redirect you to other tools and services that are not affiliated to CryptPad for the following actions:
- A password manager to have control over your passwords.
- Secure Drop for whistleblowing.
- Signal for secure real-time messaging.
📚 References
About CryptPad:
- The security section in our user guide explains the use of CryptPad's security features.
- The talk “Living on the Edge with CryptPad: privacy, distributed computation, and architectures of resilience” is an extended explanation about the concepts behind CryptPad.
- We have published a white paper describing the security mechanisms and the cryptography used in CryptPad. This document is intended for people who are already familiar with cryptography.
More general:
- The surveillance self-defense guide by the Electronic Frontier Foundation (EFF)
🙋 Questions?
We are happy to help you and answer your questions regarding this blog post. You can reach us on our forum, Matrix, Mastodon, or Email.
🙏 Acknowledgements
This project is part of CryptPad Blueprints, which is funded through the NGI0 Entrust Fund, a fund established by NLnet with financial support from the European Commission's Next Generation Internet program, under the aegis of DG Communications Networks, Content and Technology under grant agreement N° 101069594.
Links